Thieves 'could hack VW, Porsche, Audi cars'

Security researchers have found that many vehicles produced by the Volkswagen group – including some of the world's biggest luxury brands like Audi and Porsche – have a security flaw that could let hackers access them without a key.
Researchers from the Netherlands and the UK will this week present a paper detailing the flaw in transponders used by Volkswagen (VW) in its Audi, Porsche, Bentley and Lamborghini lines, Bloomberg reported on Friday.
Cars produced by Fiat, Honda, Volvo and Maserati may also be affected.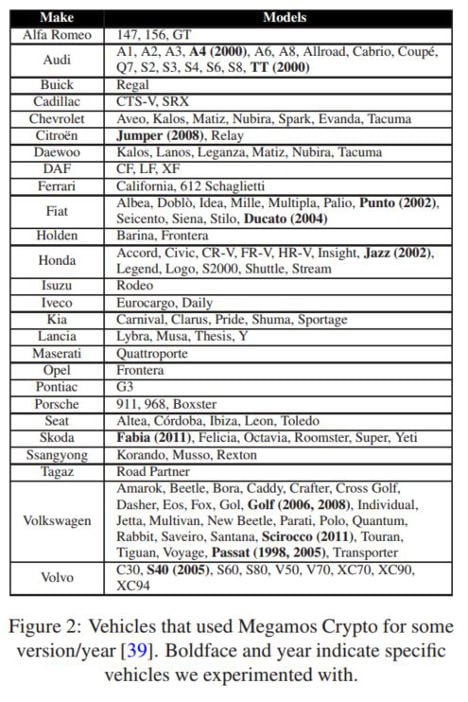
But rather than publicize and fix the problems, VW took out a court injunction against the researchers in the UK after they showed the company their findings in 2013, preventing publication.
How it works
The loophole, found by Roel Verdult and Baris Ege of Radboud University and Flavio Garcia of the University of Birmingham, targets Megamos Crypto immobilizer transponders, one of the most common brands.
Immobilizers stop the car's engine from starting unless the correct key fob is close to the car's sensors and are used in modern cars with a "start engine" button rather than a turn-key ignition.
"We have reverse-engineered all cryptographic mechanisms of Megamos Crypto... furthermore, we have identified several weaknesses in Megamos Crypto which we exploit in three attacks," the scientists wrote.
In one of the attacks they developed, the researchers used "brute force" - simply writing a computer program to try every possible combination of cryptographic keys – to break into cars in less than half an hour.
Not yet a widespread method
"This isn't a very realistic way of stealing cars" at the moment, security expert Dr David Oswald told The Local.
"For every one of these attacks, you have to speak with both the car and the key at least once. You need to get close."
In most electronically-assisted thefts carried out today, Oswald said, thieves gain physical access to the car before connecting a computer or other device through the vehicle's On-Board Diagnostics (OBD) port, which provides access to the car's computer.
However, Oswald warned that "in the long term, it would definitely make sense to change the transponder. One should always make all components secure."
While private car owners might not be at risk from the technique immediately, Oswald pointed out, there are cases where it would be easier for thieves to access both car and key fob wirelessly – for example, if a criminal rented a car he planned to steal later.
"There are technical solutions that are relatively secure that are available immediately," Oswald said, although they would require physically changing components on every vehicle currently fitted with the Megamos transponder.
For now, while consumers could avoid buying cars fitted with the affected security system, "many other similar systems are not particularly secure either," Oswald warned.
VW says risk is low
In an emailed statement on Friday, a VW spokesman told The Local that “the thresholds for protection against theft are always being lifted... the ignition lock on some older models of vehicle doesn't match that on our current vehicle modules. That's unavoidable.”
But he added that "even on older models from our product range like the ones the authors' work addressed, the attacker would need at least one key and notes on at least two successful ignitions.”
Similar cases across many different fields of IT security have seen researchers heavily criticize companies for gagging their colleagues rather than fixing loopholes, as happened in this case with the UK injunction.
"The court proceedings with the universities and the authors before the High Court in London about publication of the article was ended with an amicable compromise," the VW statement read.
"The authors are permitted to publish a part of their scientific work."
The paper has now been published with one sentence redacted, which the researchers say contained a detailed description of calculations performed by the Megamos chip.
"Volkswagen always builds the most modern, technically up-to-date security technology into its vehicles," the statement continued.
But VW added that while it offers software updates where necessary, it is "usually not possible" to update hardware components.
This article was updated on 14/08/2015 with the emailed statement from Volkswagen.
Comments
See Also
Researchers from the Netherlands and the UK will this week present a paper detailing the flaw in transponders used by Volkswagen (VW) in its Audi, Porsche, Bentley and Lamborghini lines, Bloomberg reported on Friday.
Cars produced by Fiat, Honda, Volvo and Maserati may also be affected.
But rather than publicize and fix the problems, VW took out a court injunction against the researchers in the UK after they showed the company their findings in 2013, preventing publication.
How it works
The loophole, found by Roel Verdult and Baris Ege of Radboud University and Flavio Garcia of the University of Birmingham, targets Megamos Crypto immobilizer transponders, one of the most common brands.
Immobilizers stop the car's engine from starting unless the correct key fob is close to the car's sensors and are used in modern cars with a "start engine" button rather than a turn-key ignition.
"We have reverse-engineered all cryptographic mechanisms of Megamos Crypto... furthermore, we have identified several weaknesses in Megamos Crypto which we exploit in three attacks," the scientists wrote.
In one of the attacks they developed, the researchers used "brute force" - simply writing a computer program to try every possible combination of cryptographic keys – to break into cars in less than half an hour.
Not yet a widespread method
"This isn't a very realistic way of stealing cars" at the moment, security expert Dr David Oswald told The Local.
"For every one of these attacks, you have to speak with both the car and the key at least once. You need to get close."
In most electronically-assisted thefts carried out today, Oswald said, thieves gain physical access to the car before connecting a computer or other device through the vehicle's On-Board Diagnostics (OBD) port, which provides access to the car's computer.
However, Oswald warned that "in the long term, it would definitely make sense to change the transponder. One should always make all components secure."
While private car owners might not be at risk from the technique immediately, Oswald pointed out, there are cases where it would be easier for thieves to access both car and key fob wirelessly – for example, if a criminal rented a car he planned to steal later.
"There are technical solutions that are relatively secure that are available immediately," Oswald said, although they would require physically changing components on every vehicle currently fitted with the Megamos transponder.
For now, while consumers could avoid buying cars fitted with the affected security system, "many other similar systems are not particularly secure either," Oswald warned.
VW says risk is low
In an emailed statement on Friday, a VW spokesman told The Local that “the thresholds for protection against theft are always being lifted... the ignition lock on some older models of vehicle doesn't match that on our current vehicle modules. That's unavoidable.”
But he added that "even on older models from our product range like the ones the authors' work addressed, the attacker would need at least one key and notes on at least two successful ignitions.”
Similar cases across many different fields of IT security have seen researchers heavily criticize companies for gagging their colleagues rather than fixing loopholes, as happened in this case with the UK injunction.
"The court proceedings with the universities and the authors before the High Court in London about publication of the article was ended with an amicable compromise," the VW statement read.
"The authors are permitted to publish a part of their scientific work."
The paper has now been published with one sentence redacted, which the researchers say contained a detailed description of calculations performed by the Megamos chip.
"Volkswagen always builds the most modern, technically up-to-date security technology into its vehicles," the statement continued.
But VW added that while it offers software updates where necessary, it is "usually not possible" to update hardware components.
This article was updated on 14/08/2015 with the emailed statement from Volkswagen.
Join the conversation in our comments section below. Share your own views and experience and if you have a question or suggestion for our journalists then email us at [email protected].
Please keep comments civil, constructive and on topic – and make sure to read our terms of use before getting involved.
Please log in here to leave a comment.